 I attended TechEd 2014 back in May of this year and there was one session that I wanted to share called “TWC: Pass-the-Hash and Credential Theft Mitigation Architectures”. The part from the session that I wanted to focus on was regarding administrative privileges. Credential theft has become a serious problem in today’s world where everyone is doing business online. While the internet has allowed us the ability to be more connected it also puts us at the risk of becoming a victim of cybercrime.
I attended TechEd 2014 back in May of this year and there was one session that I wanted to share called “TWC: Pass-the-Hash and Credential Theft Mitigation Architectures”. The part from the session that I wanted to focus on was regarding administrative privileges. Credential theft has become a serious problem in today’s world where everyone is doing business online. While the internet has allowed us the ability to be more connected it also puts us at the risk of becoming a victim of cybercrime.
Being an administrator in today’s corporate world you have to make sure that you are doing everything you can to protect your company’s digital assets. You have to defend against every possible intrusion while an attacker only has to be successful at finding a vulnerability one time. The TechEd session provided some good ways of how you can lower your chance of becoming a victim of credential theft.
First, let me give you some background on what Pass-The-Hash is about. The “Pass-the-Hash” phrase comes from the ability to steal a password hash and reuse it to connect to other computers. A hash is created based off your password and is used for authenticating you across the network. It will only change when you change your password. The password hash gets stored in memory and allows you to access other resources on the network without having to type in your credentials every time. If someone is able to obtain this hash then they can potentially authenticate as you.
This becomes extremely dangerous when we are talking about local or domain administrator accounts. If you use the same password for the local administrator account on all your computers then an attacker only has to steal the password hash one time and can then use it to access other computers on the network. A password hash can only be used for a network login. It will not work for an interactive login.
In order for an attacker to steal your password hash using the Pass-The-Hash method, they will have to gain local administrative rights on your computer. If they cannot gain administrator equivalent access then they will not be able use this technique. You should use the method of least privilege and never allow users to have administrative rights if possible. A user can be easily tricked into downloading a piece of malware that can allow an attacker to have access to your network. A domain admin account should never log into a standard workstation that accesses the internet or email. If your domain administrator credentials are captured then you have given the attacker the keys to the kingdom. Don’t make it easier for someone to take control over your network.
Removing admin rights can be a challenging task within a corporate environment. Users most of the time think that you do not trust them or that you are trying to exercise your power. Corporate politics can also sometimes influence security decisions. It is our duty as systems administrators to make our users and management understand the importance of restricting administrative rights. You might not be the most liked person but it is better to know that you are doing what is needed to protect your company or organization.
The presentation broke down computers and accounts into three different tiers. You have Tier 0 at the top which would be your core servers like domain controllers and domain admin accounts. This would be the most restrictive tier. Tier 1 would be your application servers and contain your server admin user accounts. Finally, Tier 2 would be your workstations and users that have access to internet and e-mail. You should never login with an account on a lower tier that has access to a higher tier. For example, an account with access to servers or domain controllers should not login to a workstation that has access to the internet. Microsoft also recommends having separate admin workstations that do not access the internet or e-mail for your domain admin account. This will help prevent your admin machine from becoming compromised.
Microsoft has created a document that discusses credential theft using Pass-The-Hash and ways to mitigate it. Please visit the links below to see more detail since I will not be able to cover everything from the presentation and whitepapers. It is well worth the time to learn more about this problem and ways to address it. They also mentioned in the presentation that this is not a flaw or vulnerability that can be addressed with a patch. Most operating systems rely on password hashes and we as administrators must take the steps to make them as secure as possible.
Link to the presentation:
http://channel9.msdn.com/Events/TechEd/NorthAmerica/2014/DCIM-B213#fbid=
Link to document discussing Pass-the-Hash attacks:
http://www.microsoft.com/en-us/download/details.aspx?id=36036
 Today wraps up a week of full-time testing of the Elitebook Folio 1040. I survived Microsoft TechEd this week without a Mac. There were some bumps along the road, but the overall experience was a good one with this new laptop. The Elitebook Folio 1040 hardware is very impressive. Some of the highlights for me have to be the battery life, the fingerprint scanner for login and passwords and the resolution of the screen. I also love the weight, or lack of weight actually, for this system. It’s extremely portable.
Today wraps up a week of full-time testing of the Elitebook Folio 1040. I survived Microsoft TechEd this week without a Mac. There were some bumps along the road, but the overall experience was a good one with this new laptop. The Elitebook Folio 1040 hardware is very impressive. Some of the highlights for me have to be the battery life, the fingerprint scanner for login and passwords and the resolution of the screen. I also love the weight, or lack of weight actually, for this system. It’s extremely portable.
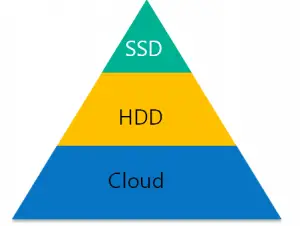 Microsoft’s Marc Farley offered one Microsoft solution during his session, The StorSimple Approach to Solving Issues Related to Growing Data Trends. Utilizing StorSimple, a Microsoft owned company, businesses can implement a third tier of storage in the cloud. But storing data in the cloud comes with its own set of challenges. The folks behind StorSimple recognized that most data in the cloud is stored in objects – not file and block like traditional datacenter data. Moving data back and forth between the cloud presents problems because you have to change the data type from file or block into objects going into the cloud and from objects back to file or block from the cloud. StorSimple is a solution to that problem by natively storing the data in object stores locally and providing companies with the ability to transport these objects into the cloud for backup, archive and off-site storage all the while providing applications with fast access to the data on-premise.
Microsoft’s Marc Farley offered one Microsoft solution during his session, The StorSimple Approach to Solving Issues Related to Growing Data Trends. Utilizing StorSimple, a Microsoft owned company, businesses can implement a third tier of storage in the cloud. But storing data in the cloud comes with its own set of challenges. The folks behind StorSimple recognized that most data in the cloud is stored in objects – not file and block like traditional datacenter data. Moving data back and forth between the cloud presents problems because you have to change the data type from file or block into objects going into the cloud and from objects back to file or block from the cloud. StorSimple is a solution to that problem by natively storing the data in object stores locally and providing companies with the ability to transport these objects into the cloud for backup, archive and off-site storage all the while providing applications with fast access to the data on-premise. For the next week, I really want to try and give the Elitebook Folio a good run through and the only way for me to do this for sure is to leave my Mac behind. I’m writing this post on the new Elitebook and I can already feel many similarities between it and my Mac. The keyboard is very familiar to a Mac user. The display is great in terms of resolution and brightness. The trackpad is different – enough so that HP packages a how-to video about the trackpad, but as a Mac user I do miss multi-touch jestures. When I unpacked the Elitebook, I was very impressed with how lightweight but sturdy the hardware felt. I promise a full review of the hardware after I’ve given it a solid test.
For the next week, I really want to try and give the Elitebook Folio a good run through and the only way for me to do this for sure is to leave my Mac behind. I’m writing this post on the new Elitebook and I can already feel many similarities between it and my Mac. The keyboard is very familiar to a Mac user. The display is great in terms of resolution and brightness. The trackpad is different – enough so that HP packages a how-to video about the trackpad, but as a Mac user I do miss multi-touch jestures. When I unpacked the Elitebook, I was very impressed with how lightweight but sturdy the hardware felt. I promise a full review of the hardware after I’ve given it a solid test.