I had the privilege of covering the Ransomware Attacks session for Commvault Connections 2022. During the event I was able to Live Tweet the sesssions. This post is a recap of the sessions. I hope it is informative and helps you understand what ransomware is and how Commvault can help you prevent these attacks for affecting your business.
Session One – Developing Your Zero Loss Strategy
This session was presented by:
Carol Clark – Vice President, Product and Solutions Marketing, Commvault
Don Foster – Vice President, Global Productivity & Evangelism Enablement, Commvault
Ransomware has continued to be the number one conversation with customers throughout 2022. Bad actors are more sophisticated than ever. As you can see in the stats below, Ransomware can have a devastating affect on a business.
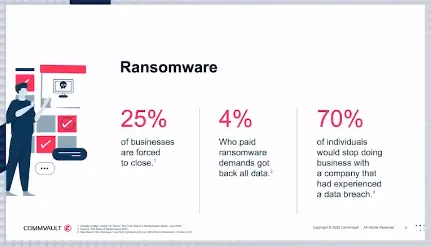
So what about the costs of Ransomware?
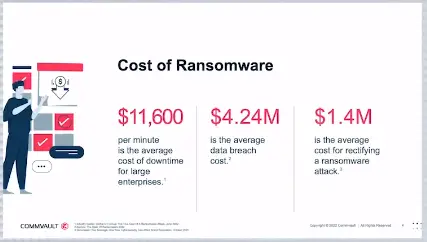
Those figures are amazing to me and paying out that kind of money could easily put a company our of business. Did you know that 1 in 3 organizations have been successfully attacked more than once? So what should you do to defend yourself from Ransomware attacks? Part of the defense should be an Incident Response Plan.

Traditionally, an Incident Response Plan is Disaster Recovery and Business Continuity. SLAs? RTOs? While these are still important, it has shifted to a whole other idea of the incident response plan: an integrated response with your security operations center. The what should then lead you to who?

Gartner is stating that organizations across the globe are starting to invest in cross-functional IT resiliency teams. By 2024, 45% of enterprises will have built specific cross-functional teams across their organization to meet the threat of ransomware head on. So where do you start? With a Zero Loss Strategy. A zero loss strategy is a plan to better manage and reduce the impact of ransomware and cyber attacks. Here are the fundamentals of a zero loss strategy.
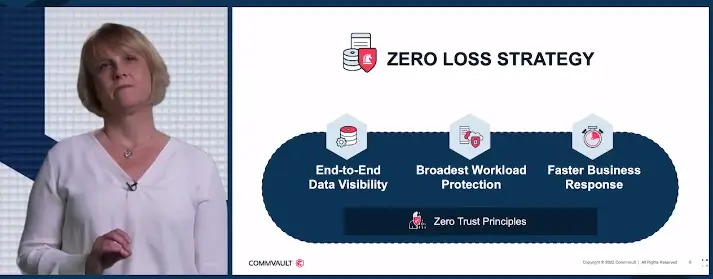
End-to-End Visibility, what is the best visibility to identify data?

How about the Broadest Workloads? You need to protect what matters most.

Finally what about a faster business reponse? You need to ensure a proactive recovery.

So what are the Zero Trust Principles that make up the zero loss strategy? Multi layered security concepts as mentioned below.

In summary, what is an effective plan with a zero loss strategy consist of? The right people, the right process and the right technology.

Session Two – Trailblazing Data Security: Safeguarding Data Before It’s Compromised
This session was presented by
Steve Preston – Vice President, Metallic Security Services, Commvault
Zack Brigman – Senior Manager, Metallic Product Marketing and Programs, Commvault
This presentation centers around how Commvault can strengthen customer security with their Metallic product line. A quick glance of this is shown below.
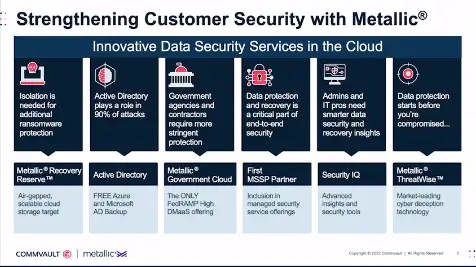
Metallic ThreatWise is the latest offering to help Commvault customers protect themselves from Ransomware.
When thinking about ransomware, you need to understand how it is evolving.
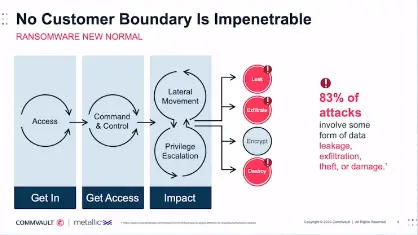
As you can see above, they will find a way in (phishing, non patched vulnerability, etc), get or create credentials in your system and start moving around to find what you have. Today, they not only go after your production data, but they also look for your backup environment. They want to take away your ability to recover so you have no choice but to pay them to decrypt your data or to get rid of the data that they stole from you (exfiltrate). This where ThreatWise comes in

ThreatWise is an early warning system for advanced attacks. Fake assets are deployed in your environment so that if a threat actor is doing their discovery and they access on of these fake assets, you would get notified and the actor would never even know that they have been detected. This process is represented in the image below.

Session Three – Ransomware Retrospective: Supporting the Recovery
This session was presented by
Mike Letschin – Senior Director, Product and Solutions Marketing, Commvault
Jordan Xu – Commvault Customer Support
Blaine Williams – Commvault Customer Support
Vincent Torro – Metallic® Support
This session shows some customer stories: how some went well and some not so much.
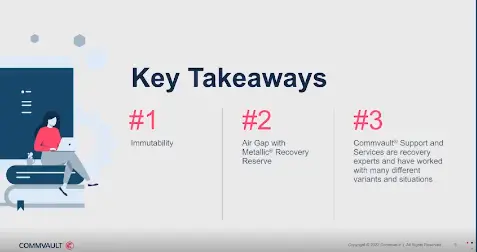
First up is a longer term ransomware recovery story. For this customer, an attacker infiltrated their systems globally and all their internal systems were disrupted. The good news for this customer is that they had Commvault’s ransomware protection enabled on their disc library in the US data center (primary and largest site). This protected their data at rest from be impacted by the ransomware and crypto lock. This allowed them to recover the affected US systems quickly using the Commvault GUI. Helping the customer with the recovery plan and guide them through the most efficient way to recover the systems. The biggest challenge for the customer was for the global data centers using Google Cloud Storage in public cloud. The bad actors were able to access their secret key and access key. That allowed the actor to delete a lot of the Commvault backup data stored there. Another challenge was limited bandwidth to satellite sites making the recovery process quite slow. To help the customer against future attacks, Metallic Recovery Reserve was recommended and implemented.
Key Takeaways from this customer story:
Next up, lets look at some challenging recoveries and the pain points experienced. In one instance, the hacker had been in a customer network for about three weeks, planning for his big day and ended up infecting 3,000 servers. Essentially, everything was down. The customer had no disaster recovery plan so whatever team yelled the loudest is who got their systems restored first. Obviously not having a recovery plan hurt them tremendously.
Key Takeaways:
You need a DR plan, one that you TEST, TEST, TEST.

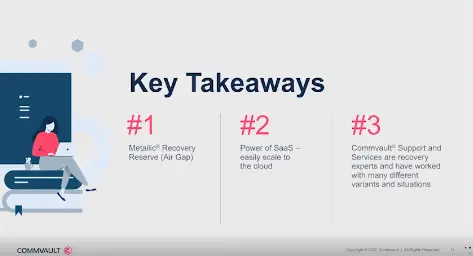
Next, lets discuss a shorter recovery story. A customer was hit with a ransomware attack and Commvault reached out them to let them know they were there to help them recover. The customer needed some time to compile the list of affected systems before starting the recovery process. 62 servers had been affected. Current scheduled backups were disabled for those servers so that there would be no compromised backups. After that, the recovery process was kicked off, starting with the most critical systems. At the 18 hour mark, 50 servers had been recovered. Three hours after that, only 4 systems were left to recover. They were back up and operational the next morning with non critical systems recovered over the weekend.
Key Takeaways:
This concludes the sessions on Ransomware. I hope this recap was informative. Make sure you join the next Commvault Connections!

