Only a small percentage of companies think of printers when it comes to securing their network, leaving them vulnerable and susceptible to attacks. Print security? Is that really such a thing? Last week, I spent the day today with HP in Palo Alto, CA, learning about secure printing solutions within their portfolio. Why HP? To me, printing has always been synonymous with HP, even moreso after company split into two companies in 2015. The new HP, Inc., is focused specifically on printing and personal systems and it has one of the largest install bases of its printers in the world.
In many ways, printers were the original thing of IoT. Printers have been network connected for a couple decades now, but the fact that they have been stable and largely ‘just work’ allows people to take them for granted. That leaves printers unpatched and unsecured on networks, which could be a gateway for malicious activity. Add to the mix that printers are also unmonitored and you have a winning combination for hackers to play.
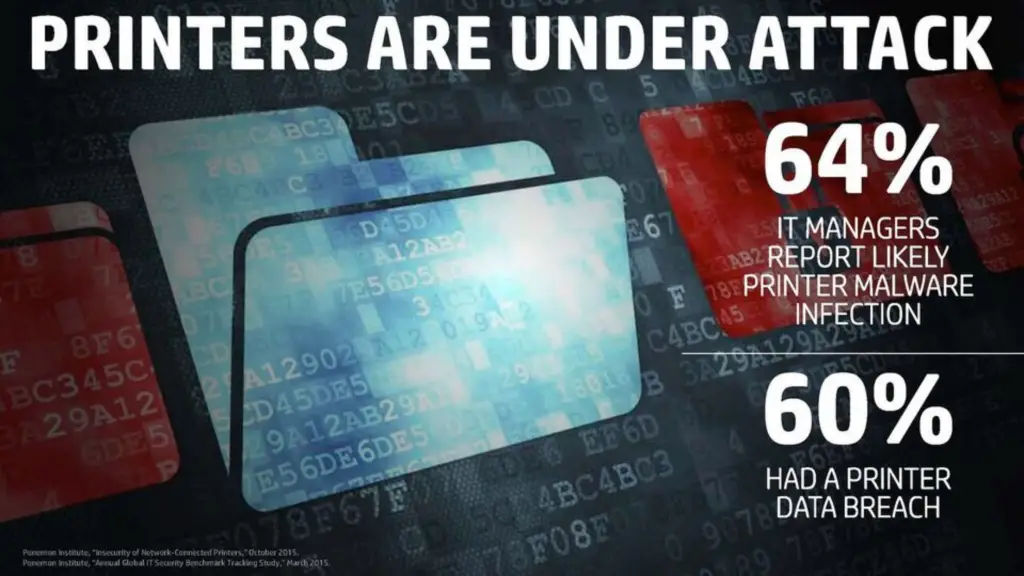
Printers have changed in recent years to keep up with the mobile revolution – adding WiFi, their own email addresses, connections to cloud services, and even apps inside of them – and the build-out of printers software has increased attack surface and the number of potential vulnerabilities. WiFi and wired connectivity on the same device makes it possible to bridge a network. WIRED posted a story almost 18 months ago that outlined hackers creatively using drones to fly phones and connect wirelessly to printers in an office building, then bridging the network, and injecting code for a backdoor onto the network while bypassing the company’s firewalls.
At the HP event, hacker Michael Calce, aka MafiaBoy, spoke with our group of bloggers. Calce was the infamous hacker who took down CNN and Yahoo in 2000 using a distributed denial of service (DDOS) attack. It was unlike anything the Internet had seen before and Calce was only 15. Some years later, Calce switched sides and became a security consultant – advising and providing penetration test services to customers.
Calce spoke for a long time about the mindset of a hacker. “Hackers don’t think the same as regular people,” he reiterated multiple times during his presentation and during discussions throughout the day. The mindset of a hacker is first to understand how you are going to use technology, but then to find ways to circumvent and utilize it for their own purposes. During his first years of hacking, it was all about ‘look at me’ and showing off. Today, however, the goal of hacking is all about monetary gain and these hackers have found funding from sponsor states and free reign to do their bidding. In short, they’re incented.
 The main piece of advice from Calce for companies to to educate their employees. According to him, employees are the weakest link and without fail, social engineering and spear phishing are his go-to methods for infiltrating companies during pen-tests. Education programs can come in many shapes and forms, but the primary intent is awareness and changing employee behavior to be more cautious about attachments, documents, and links they receive.
The main piece of advice from Calce for companies to to educate their employees. According to him, employees are the weakest link and without fail, social engineering and spear phishing are his go-to methods for infiltrating companies during pen-tests. Education programs can come in many shapes and forms, but the primary intent is awareness and changing employee behavior to be more cautious about attachments, documents, and links they receive.
Most hackers, according to Calce, are not coming through your front door or your back door. He likened it to bank robbers – they aren’t breaking into your bank through the doorways, they are coming in through creative ways – cutting through walls or under floors. And the same is true for your network. Hackers are looking for opportunistic ways to get in through easier methods that are not protected. Printers and other connected devices are easy targets for those attacks since they are not secured like other parts of the network.
Printers are an endpoint, just like your PC, Servers, storage and network equipment. So, what are you to do? I’ve got 5 ways you can improve your printer security for free. Check out my next blog post.
Disclaimer: HP, Inc., invited me to this blogger tech day and paid for my travel and hotel accommodations. This blog post, however, is my own views and opinions based on the information that was presented. HP did not review or advise what to say or how to say it – these are my own words.
