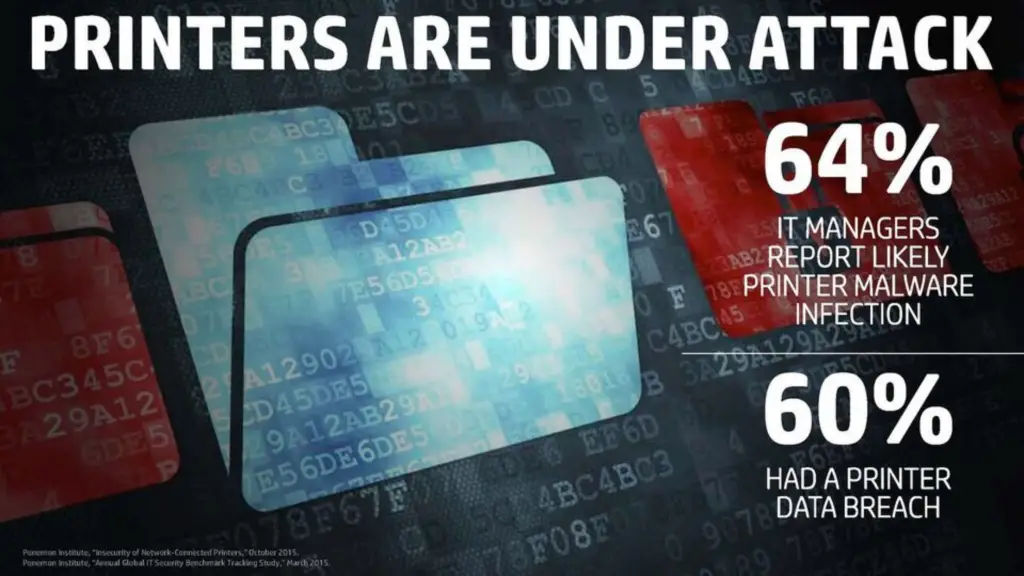
So, you’re sufficiently concerned about security for your printing environment. What can you do to immediately improve your situation? And secondly, how much is it going to cost you? Let’s take a look at some general tips that you can accomplish with no additional expense.
Tip 1: Check for patches to your firmware and BIOS and patch your printers software.
This may seem like an obvious one, but the fact remains that a majority of companies do not have a regular patching plan for their printers. When talking with them about their servers and workstations, there are plans and procedures for patching and maintaining that software. When you talk with them about other infrastructure, like networking and storage, there is an awareness and proactivity to patch and upgrade these devices – for features and to rid themselves of bugs. But its not so for printers.
While on the topic, you should also ensure that you get your patches and upgrades directly from the vendor’s website. Third party sites could host modified firmware and BIOS that has malicious code. Relatively few printers checksum or validate their code before running it. It may be a good idea to audit and check the code running on your printers to ensure it is authentic and it has not been tampered with.
Tip 2: Disable any services that you do not require on the devices.
Just like companies have build standards for servers, networking and storage, your printers should also have a standard build profile. This profile should remove any unnecessary services and leave only the ones that are truly required by the company. For instance, did you know Telnet and FTP are often enabled on printers by default? When was the last time you needed to Telnet or FTP to a printer? Should you allow HTTP or only HTTPS? Develop a build document for standardizing your printer fleet. Disable any service that is not used or needed to avoid open doorways for malicious activity.
Tip 3: Change those default passwords!
This really should be second nature, but again, most companies do not have a build standard and therefore default passwords exist in the wild – in the wild and even connected directly to public IP addresses. So, the first line of defense is to change known passwords so that if your printer is ever made accessible, it is not an easy target with a known password. Also, adhere to your normal password policies for complexity and length to ensure a good password is installed on all of your devices.
Tip 4: Monitor your devices – tap into logs and/or SNMP
You should use SNMP to setup alerting from the device and also allow secure polling of the device from management software. While there have been a few known vulnerabilities in printers via SNMP, patching should allow you to safely implement SNMP for your printer fleet. SNMP should be configured to forward traps to your Security Information Event Management (SIEM) software and also to allow SIEM to poll and retrieve information from the device. The traps should alert you to conditions, and although capabilities my vary by vendor and printer, you should be able to find out when new code is loaded, when toner is running low and other useful conditions.
Secondly, if you have the ability to reach in and obtain the logs of the printer, this is valuable information from a forensics and analysis standpoint. The logs should have records for any new code added, any reboot requested, and should lead you with information about source IP and the account used for any of these operations. During my event with HP last week, the question was asked – “If a printer was used to compromise your network, would you know?” Monitoring is the only way to know.
Tip 5: Investigate printer specific monitoring and management software
Most printer vendors give away free monitoring and management software as a value-add to their customers. This software often becomes ‘shelf-ware’ and never gets implemented. That’s a critical mistake. The management software may be a big help in accomplishing all 4 of the prior tips. Rather than having to manually reconfigure and secure each printer, a free vendor software, such as HP’s Web Jetadmin, may be available for your use.
Ok, what next?
So, after implementing these tips, you can go further and deeper to secure your printing fleet. In HP’s case, they have a full suite of software under the JetAdvantage branding to help enterprises combat and ensure that their printer fleet is secure. For more information about those products, see http://www.hp.com/go/jetadvantage and check out my next blog post.
Disclaimer: HP, Inc., invited me to their Palo Alto headquarters and paid all expenses associated with this educational trip. This blog post is a result of that trip and the information shared, however, the information I have written in this post is solely written by me without any editorial input from HP.
 The main piece of advice from Calce for companies to to educate their employees. According to him, employees are the weakest link and without fail, social engineering and spear phishing are his go-to methods for infiltrating companies during pen-tests. Education programs can come in many shapes and forms, but the primary intent is awareness and changing employee behavior to be more cautious about attachments, documents, and links they receive.
The main piece of advice from Calce for companies to to educate their employees. According to him, employees are the weakest link and without fail, social engineering and spear phishing are his go-to methods for infiltrating companies during pen-tests. Education programs can come in many shapes and forms, but the primary intent is awareness and changing employee behavior to be more cautious about attachments, documents, and links they receive. For the first time in forever, HP has birthed a new line and brand of printers – well, sort of. A couple of years go, HP introduced the OfficeJet Pro X line of printers. These printers looked a lot like a LaserJet printer, they were built for business, but the actual print tech was more closely related to an inkjet, and so they were placed in the OfficeJet line. But, there was so much different than other OfficeJet printers. These printers didn’t use a moving print head, they didn’t use the same type of ink and the print speeds were much faster than any other inkjet. This was all enabled because of a print bar that spanned the entire width of the page – something HP dubbed PageWide Technology – and pigmented ink.
For the first time in forever, HP has birthed a new line and brand of printers – well, sort of. A couple of years go, HP introduced the OfficeJet Pro X line of printers. These printers looked a lot like a LaserJet printer, they were built for business, but the actual print tech was more closely related to an inkjet, and so they were placed in the OfficeJet line. But, there was so much different than other OfficeJet printers. These printers didn’t use a moving print head, they didn’t use the same type of ink and the print speeds were much faster than any other inkjet. This was all enabled because of a print bar that spanned the entire width of the page – something HP dubbed PageWide Technology – and pigmented ink.


