The concept of a digital twin model is something new to me, but you and I likely use one every day, without knowing a name for it. When was the last time that you used Google Maps, Apple Maps or Waze for directions or to chart a path or to check traffic? Each of these is a digital twin, representing the physical roads and buildings in our world in a digital form with data overlayed to assist with common tasks.
Forward Networks is creating the same digital representation of your network infrastructure, gleaning the configurations from your network devices and then assembling a representation of all the devices and their links. Just like the maps listed above, the base layer of representation are the intersections and the roads the extend from those intersections. This is your network devices and the connections that extend between them.
From the base layer, you can compute best paths between two points, look at all paths between two points and make some basic computations about optimized path. But the value does not stop with the computation of paths and best directions between two point.
Just like the map apps above, the digital twin can layer on additional context – such as traffic with the maps application or such as metrics like bandwidth and utilization and other metrics from the network devices.
During Cloud Field Day 16, I had to chance to learn a bit more directly from co-founder Peyman Kazemian. CFD16 was hosted onsite at Forward Networks’ headquarters in Santa Clara, CA. After sharing the basis of the digital twin network, Kazemain dove deeper into how customers can leverage the network and benefit from its capabilities.
Network Query Engine
Forward has created a query engine, where you can quickly ask questions and investigate data collected in the Forward Network model. The Network Query Engine is the primary power of the Forward Networks platform. Everything about the network is represented in the model and accessible to query, in a SQL-like language.
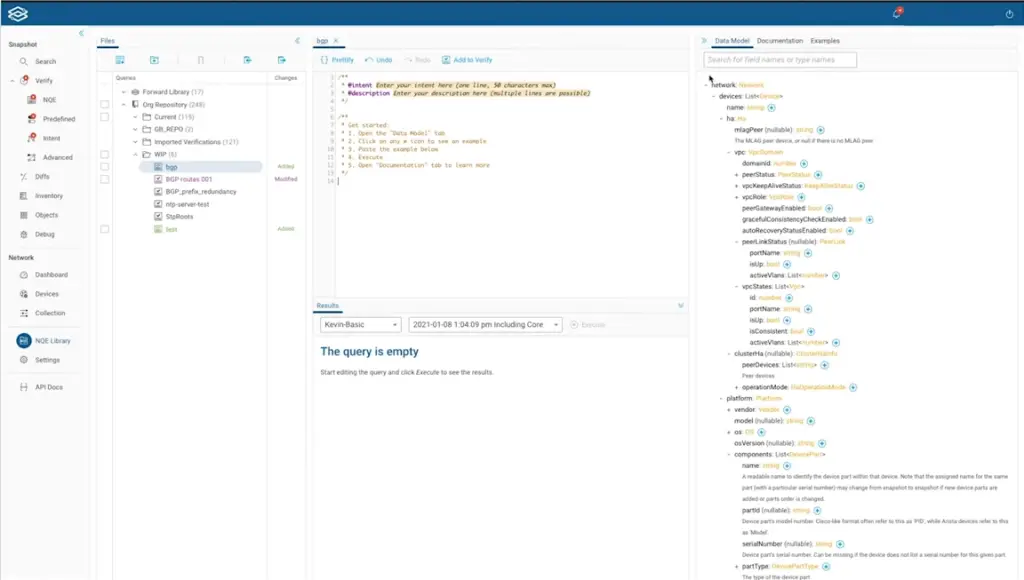
The query is very staightforward using language like
foreach device in network.devices
foreach interface in device.interfaces
select {
devicename: device.name,
interfacename: interface.name
}The model is visible and can be expanded to find the elements you want to include and name. Often, when products have their own search language, this is the biggest barrier to usage – what elements and what language is used?
Output and Tests
The power of the platform is the computed paths for the network. For instance, can traffic pass from a source IP to a destination IP and port with the current configuration or do you need to adjust firewall rules or routing to allow this traffic to pass?
Forward is able to test the traffic on the digital twin network. It is able to use the active configuration and show the place where the traffic is going to fail and pinpoint that for easier reconfiguration or changes. Oft times, as an infrastructure administrator, you go to the network team with an issue but the network is an unknown to you. Being informed with the exact point where the failure is occurring can assist in time to resolution.
Other times, the network team needs to go and trace and test to find where the failure occurs. More times than not, my network admins have needed to adjust and test and adjust and test and adjust and test, before finding the winning combination – sometimes breaking things in the process. Forward Networks can eliminate this hunting and ensure that the changes will not cause adverse effects. Not only can Forward Networks find the failure point, it can propose the changes required that will allow it to work properly. Forward can model the results of the config changes, ensuring a clean change implementation on the production network and no interruption in service while making the necessary adjustments.
Use Cases
During Cloud Field Day 16, Jason Gintert tweeted out a great screenshot and I have it below where I quoted and gave my two cents. Preventing problems from network changes is a HUGE, game-changing use case for Forward Networks.
Pinpointing where your #network #traffic fails is a potential large #timesaving feature. Showing the changes to make it work is an exponential savings. Modeling it in a #digitaltwin network and NOT breaking #production is a game changer. @FwdNetworks makes that possible. #CFD16 https://t.co/0dmPAkJOAw
— Philip Sellers (@infraphilip) January 25, 2023
At Paypal, the team developed a Slack bot based on Forward Network’s digital twin and they called the app Pathbot. With Pathbot, any Paypal engineer can go into Slack and quickly perform a search between two IP addresses and a destination port and the twin network will compute if the traffic is able to flow and if not, directs the team where to submit a request. This simple troubleshooting is a highly effective in large and complex networks to test traffic flow between two endpoints.
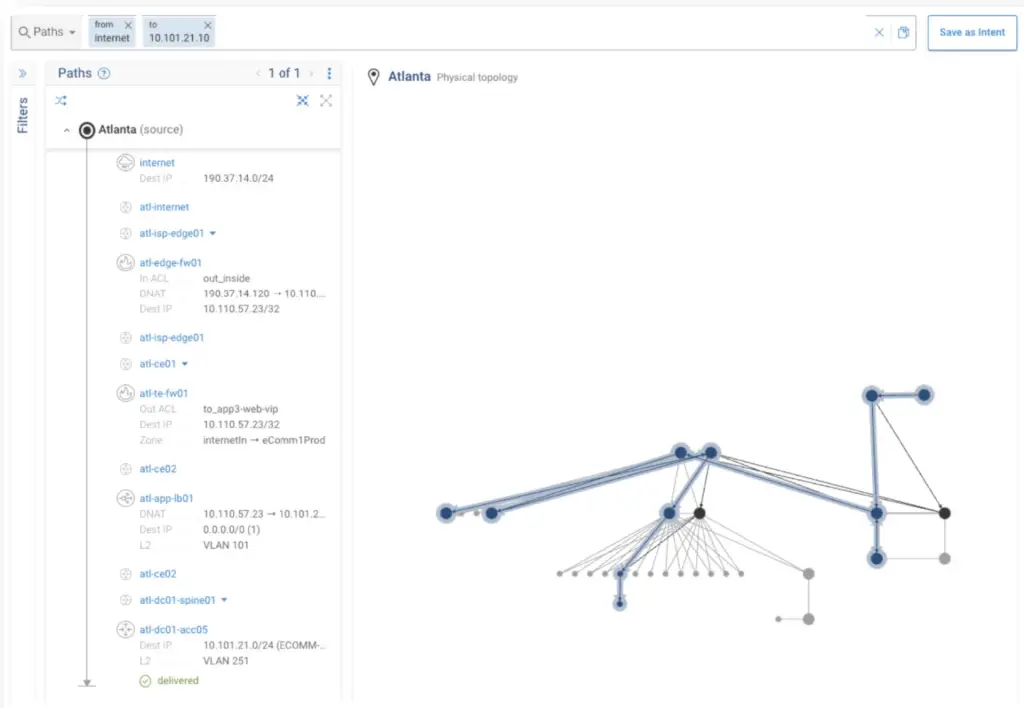
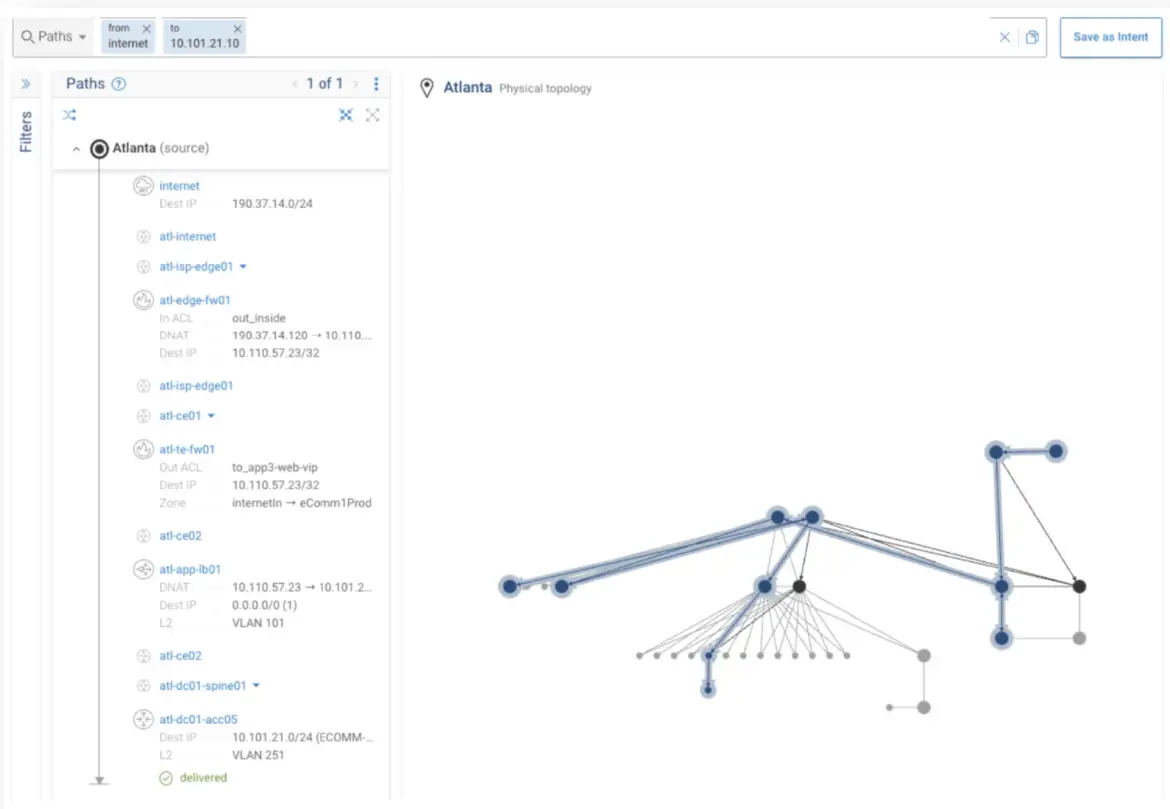
From a security perspective, Forward Networks can help with the triage of a compromised host, but mapping all accessible devices from the device. Forward refers to this as blast radius detection, illustrated below. Because Forward Networks is aware of all the endpoints by IP and can see all paths from that endpoint that it is allowed to travel, it is able to map back to any other hosts and help to see the exposure of your network. With increasingly complexity associated with intent based networking, microsegmentation and, generally, enhanced security of networks, having analysis of the network and how traffic is permitted to flow is a huge time saver.
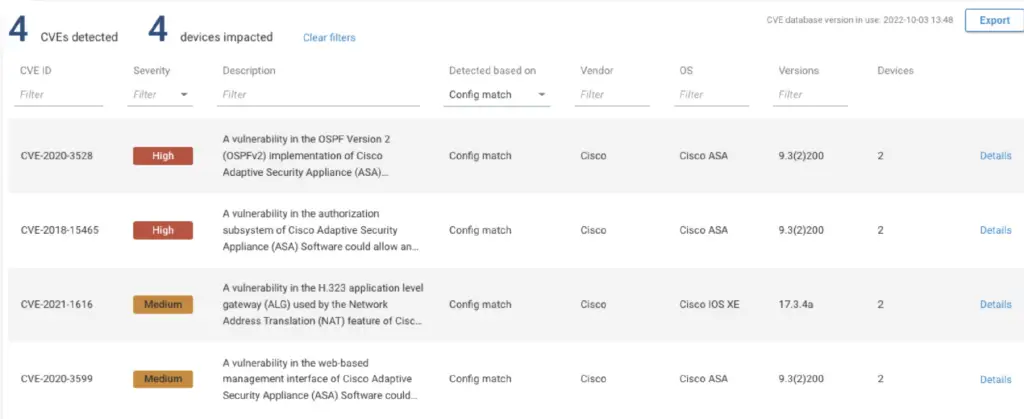
Forward Networks can also help to pinpoint CVE exposure on the network devices, as illustrated on the screenshot below. It is a rather straightforward use case, but it is a valuable one where you can look for known vulnerabilities exist in the network. But the CVE checks aren’t the only security risk that Forward is able to examine.
Perhaps more useful than the CVE checks, Forward Networks is able to check against STIGs for configured settings that do not meet the best practices. STIG checks is a huge benefit because CVEs aren’t always about patches, but about the active configuration – for instance, allowing Telnet on devices, which is not encrypted and the traffic could be intercepted.
Additional Resources
Foward Networks’ Cloud Field Day 16 Presentation
- Part 1 – https://www.youtube.com/watch?v=cIYdaSXY_mY
- Part 2 – https://www.youtube.com/watch?v=TbOqFx35QjY&t=43s
Forward Networks’ YouTube Channel – https://www.youtube.com/@ForwardNetworks
Disclaimer: Tech Field Day, an independent organization, paid for my travel and accommodations to attend Cloud Field Day 16 where these cloud-native vendors presented. The views and opinions represented in this blog are my own and were not dictated or reviewed by the vendors.
 I have had a long relationship with Hewlett Packard and now Hewlett Packard Enterprise. Today, I sat in a strategy session with Paul Miller and Mark Linesch. It is an interesting time as these two guys have transitioned into marketing roles for the whole of HPE – reacting to the transition of IT purchasing away from silos and into an holistic strategy.
I have had a long relationship with Hewlett Packard and now Hewlett Packard Enterprise. Today, I sat in a strategy session with Paul Miller and Mark Linesch. It is an interesting time as these two guys have transitioned into marketing roles for the whole of HPE – reacting to the transition of IT purchasing away from silos and into an holistic strategy. Plexxi OS, the switch software, runs on HPE/Plexxi certified switches, which are open standard switches (aka whitebox switches). The Plexxi folks I spoke with said the code would likely run on other open switch platform, however, it would not be certified and supported. Like all other open networking solutions, the secret is in the software. A controller is used to define the configuration of the network and then handle all of the ways that interconnection can occur.
Plexxi OS, the switch software, runs on HPE/Plexxi certified switches, which are open standard switches (aka whitebox switches). The Plexxi folks I spoke with said the code would likely run on other open switch platform, however, it would not be certified and supported. Like all other open networking solutions, the secret is in the software. A controller is used to define the configuration of the network and then handle all of the ways that interconnection can occur.


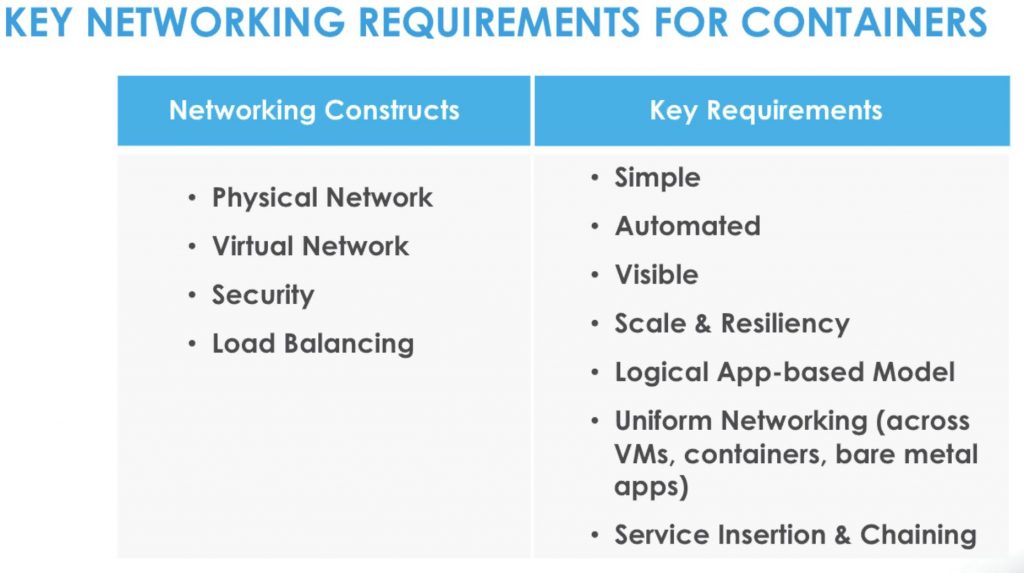
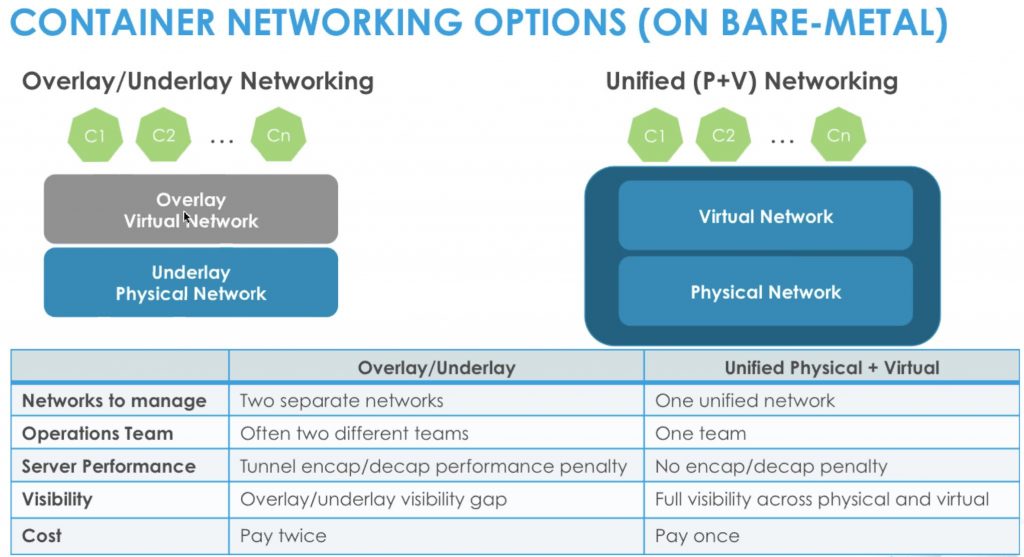
 New house. New city. New ISP. New router. This time I opted for the big brother of the EdgeRouter Lite, the
New house. New city. New ISP. New router. This time I opted for the big brother of the EdgeRouter Lite, the 


