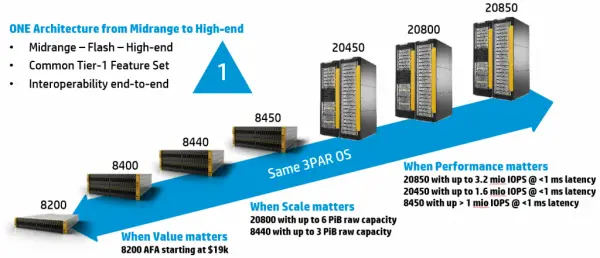
An upgrade vSphere 6.5 means no more beloved Windows/C# vSphere Client and loads of people are being forced to the web client. With the web client, certificates play a much more important role in the overall design and untrusted certificate on your vCenter and ESXi hosts will plague you when trying to deploy new VMs, import OVF’s and other upload situations. This is because those uploads talk directly to the ESXi host, so even if you’ve accepted the certificate for the vCenter and you’re uploading from vCenter, the upload itself occurs between your machine and the ESXi, whose certificate is also untrusted.
The fix is fairly simple. At vSphere 6.0, VMware introduced the VMware Certificate Authority (VMCA) as part of the Platform Services Controller component of vCenter. The VMCA has its own root certificate that is used to issue all host and service certificates in the environment. If your computer trusts the root certificate, you trust all of the issued certificates from this CA. The solution is to download and import the root certificate from your VMCA.
To do this, navigate to your vCenter’s web UI. Accept the untrusted certificate when prompted and then the Getting Started page is displayed. On the lower right side of the page, there is a link to download the trusted root CA certificates. 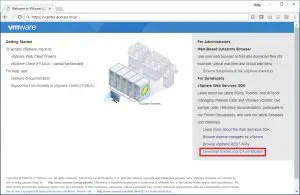
This will begin a download for a zip file. In vCenter 6.5, the zip file is organized with a certs subfolder, then subfolders by operating system. Navigate to your OS folder. In simple deployments, a single certificate will be inside of the zip file along with a .crl file or files.
For Windows, double click the .CRT file and a properties window appears. Click Install Certificate… then choose Local Machine & Next, allow the UAC if prompted, choose the Place all certificates in the following store and then click Browse…
In the window that appears, choose Tursted Root Certificate Authorities as the certificate store, then click OK. Click Next and Finish to complete the process.
A reboot may be required to activate the change, but afterwards, the pesky untrusted certificate warnings will be gone.
While at VMworld this year, I attended a great session from Adam Eckerle about certificate management in vSphere 6.5. He recommended this method, as opposed to making your VMCA a subordinate CA. Its not the first time he’s presented this information – if you’re interested, you can see the presentation from VMworld 2016 posted online for free. The 2017 session with info about 6.5 should be posted later.









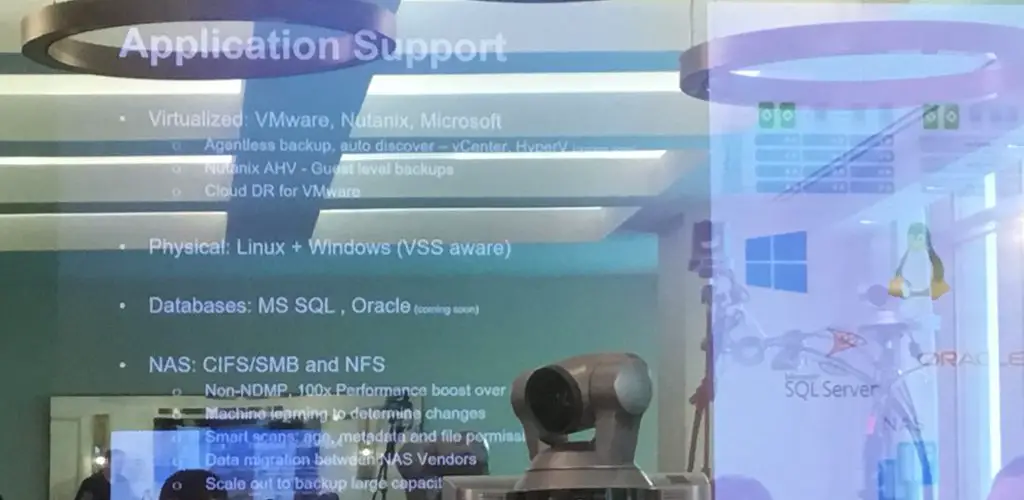



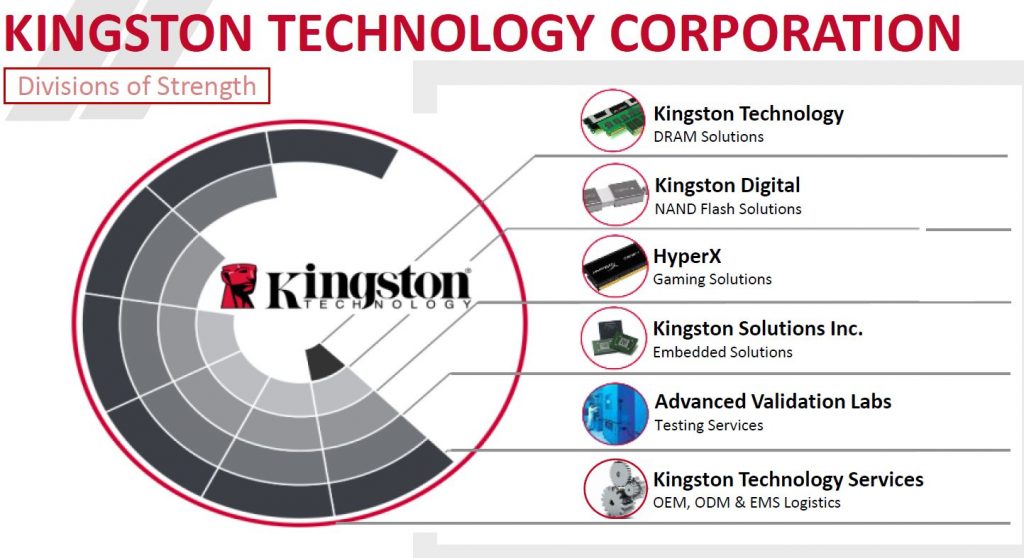

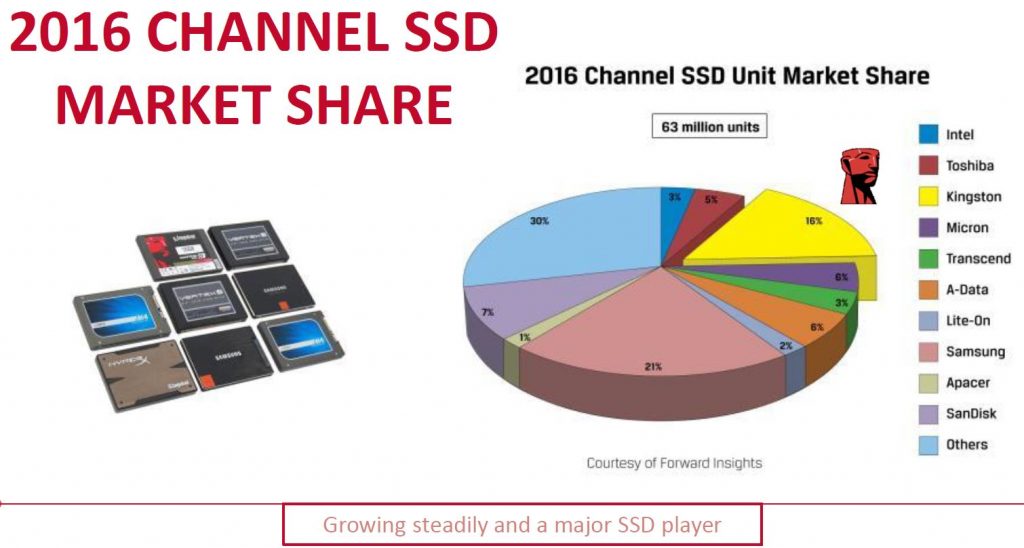
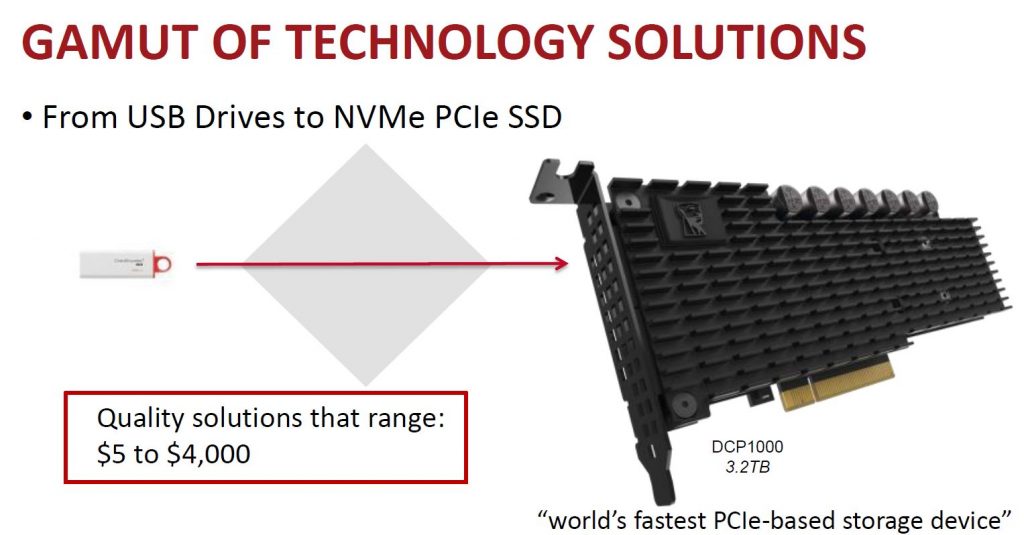

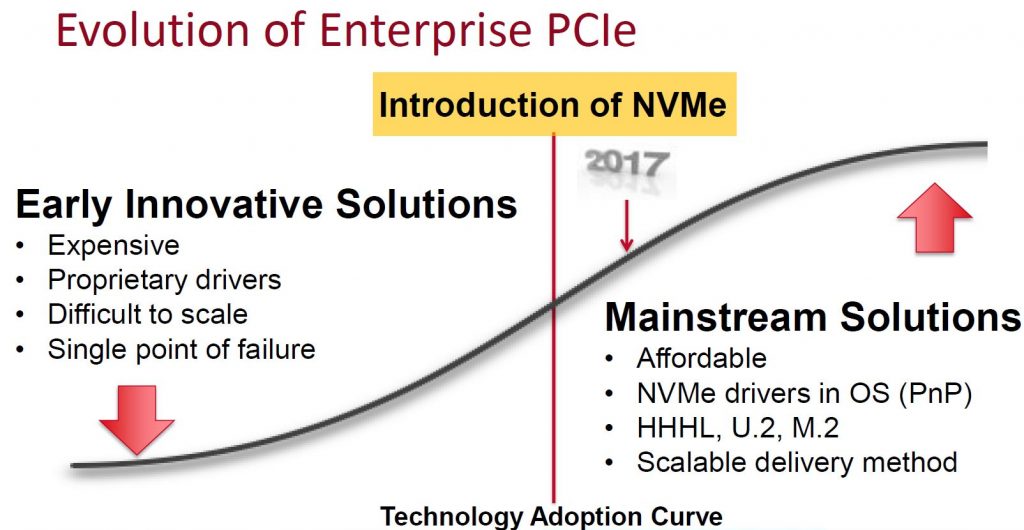
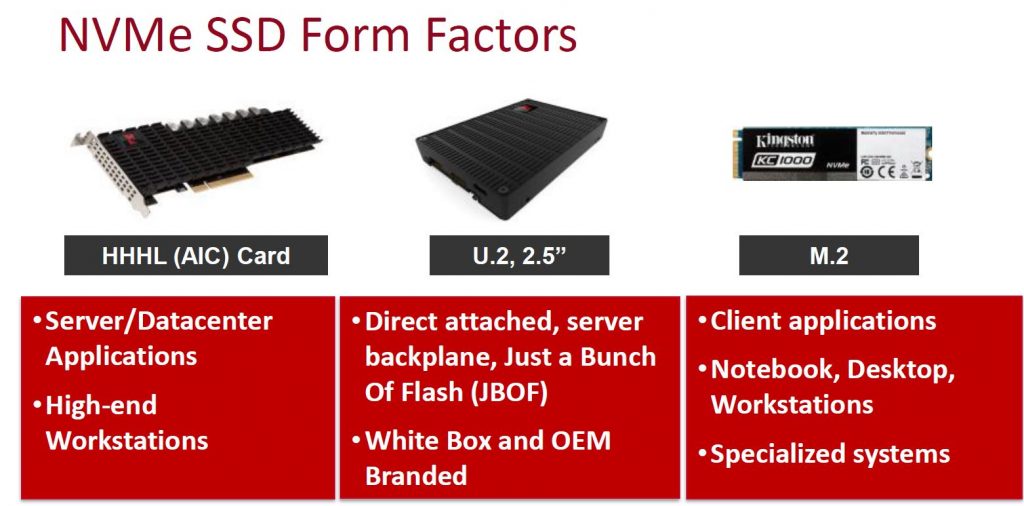


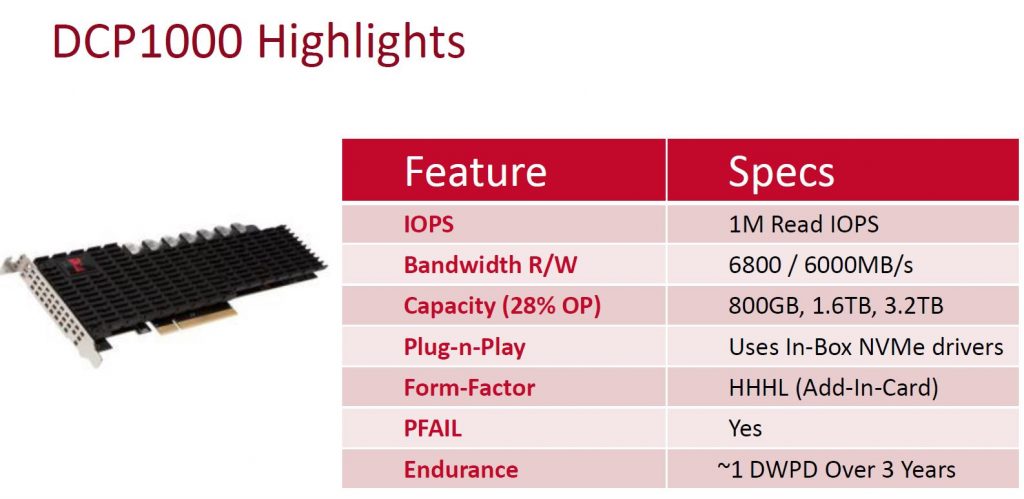
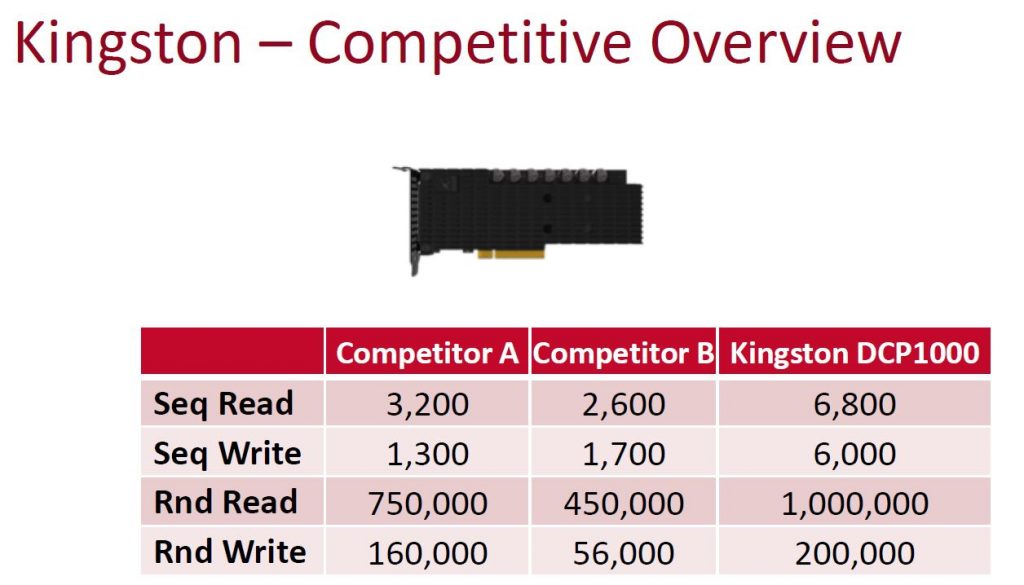

 After almost a 3 year run, HP is replacing the 3PAR StoreServ 7000 series with all new
After almost a 3 year run, HP is replacing the 3PAR StoreServ 7000 series with all new