New Data Protection Solution Strengthens StorCentric’s Data-Centric Security Portfolio
Walnut Creek, Calif.— February 15, 2022 — Retrospect™, a StorCentric company, today announced the general availability (GA) of Retrospect Backup 18.5, featuring new anomaly detection, customizable filtering and thresholds, and enhanced ransomware protection to help businesses quickly detect and protect against malicious attacks. With deeper Microsoft Azure Blob integration for Immutable Backups and integrated cloud bucket creation, Retrospect Backup 18.5’s anomaly detection and ransomware protect bolsters StorCentric’s data-centric security approach to organizations’ critical infrastructure.
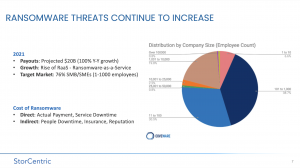
Ransomware is a huge global threat to businesses around the world. Beyond the high-profile attacks, including Colonial Pipeline, JBS, Garmin, and Acer, many people now personally know a colleague whose business was attacked. According to Coveware, most corporate targets are small and medium businesses. 72% of targeted businesses have fewer than 1,000 employees, and 37% have fewer than 100. Businesses are projected to have paid out $20B in 2021, a 100% Y-o-Y increase for the last four years, and it’s only going to get worse with new business models like RaaS: ransomware-as-a-service. With Retrospect Backup 18, businesses can protect their infrastructure with immutable backups for ransomware protection.
Beyond protection, organizations need to detect ransomware as early as possible to stop the threat and remediate those resources. Retrospect Backup 18.5 includes anomaly detection to identify changes in an environment that warrants the attention of IT. Administrators can tailor anomaly detection to their business’s specific systems using customizable filtering and thresholds for each of their backup policies, and those anomalies are aggregated on Retrospect Management Console across the entire business’s Retrospect Backup instances or a partner’s client base with a notification area for responding to those anomalies.
“As ransomware continues to grow in prevalence, businesses can leverage Retrospect’s new anomaly detection to quickly identify when ransomware has infected their infrastructure and rely on their immutable backups to restore any lost data,” said JG Heithcock, General Manager, Retrospect, a StorCentric Company. “Anomaly detection is integrated into Retrospect’s policy-based workflow and with our hosted service, Retrospect Management Console, to ensure customers and partners are notified about anomalies as soon as they happen.”
Retrospect Backup 18.5
Included in Retrospect Backup 18.5:
* Anomaly Detection: Detect anomalies in systems based on customizable filters and thresholds tailored to individual environments.
* Retrospect Management Console Integration: View anomalies across a business or partner’s entire client base in a single pane of glass.
* Improved Microsoft Azure Blob Integration: Set individual immutable retention policies for different backup sets within the same Azure Storage Container.
* Streamlined Immutable Backup User Experience: Automatically create cloud buckets with immutable backups supported by default.
* LTO-9 Support: Includes support for LTO-9, with capacities up to 18TB (45TB compressed).
Channel Partner Validation
“Ransomware comes up so frequently now that companies need tools like anomaly detection and immutable backups to detect and defend their core data from threats, and enabling IT admins to adjust the filtering and alert thresholds helps companies tailor the detection algorithm to their needs,” said Reuben Herfindahl, Owner of Digital Brigade.
“Retrospect’s new anomaly detection can help businesses proactively identify threats as soon as their backup runs. With Retrospect’s immutable backups, they know they can restore their backups if ransomware has infiltrated their network,” said Terry Noonan, License My Software LLC.
Pricing and Free 30-Day Trial
Retrospect Backup 18.5 is a free upgrade to Retrospect Backup 18, the award-winning ransomware protection solution. For Retrospect Backup pricing details, please visit: https://www.retrospect.com/store. To request a free 30-day trial, please visit: https://www.retrospect.com/try.
About Retrospect
Protecting 100 Petabytes in over 500,000 homes and businesses in over 100 countries, Retrospect provides reliable backup and recovery tools for professionals and small- to- midsize businesses with Retrospect Backup and Retrospect Virtual, covering physical servers and endpoints, virtual environments, and business applications. With three decades of field- tested expertise, Retrospect meets the needs of organizations that require the highest level of recoverability. Retrospect is a proud member of the StorCentric family of brands. For further information, please visit: www.retrospect.com.
About StorCentric
StorCentric provides world-class and award-winning storage solutions. Between its Drobo, Nexsan, Retrospect and Vexata divisions, the company has shipped over 1M storage solutions and has won over 100 awards for technology innovation and service excellence. StorCentric innovation is centered around customers and their specific data requirements, and delivers quality solutions with unprecedented flexibility, data protection, performance and expandability. For further information, please visit: www.storcentric.com.